By using the Storage Settings option, users can configure automatic management of .etl or .log files stored by Elipse Software systems. With it, users can manage where log files are stored, the maximum size of the repository, and the time each file is kept on the repository, based on a file's creation date. To use this option, select the View - Storage Settings menu or click Storage Settings ![]() on the toolbar to open the window on the next figure.
on the toolbar to open the window on the next figure.
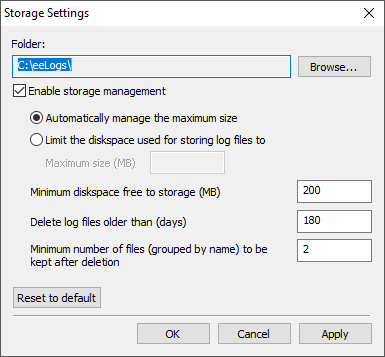
Storage Settings window
NOTE |
Be careful when disabling the repository with value 0 (zero) in the Limit the diskspace used for storing log files to option, because if the Enable storage management option is selected, management leaves the repository with a minimum number of files (by name pattern, pre-defined as 2) as soon as this option is confirmed by clicking OK or Apply. |
The available options on this window are described on the next table.
Available options on the Storage Settings window
Option |
Description |
|---|---|
Folder |
Shows where logs are stored |
Browse |
Allows selecting the folder where logs are stored |
Enable storage management |
Enables repository management. When this option is selected, repository management routines are activated |
Automatically manage the maximum size |
The log system calculates the available limit based on a partition's free space to manage logs. The rule for allocating space in automatic mode is using 25% (twenty-five percent) of a partition's free space |
Limit the diskspace used for storing log files to |
Specifies the maximum available size for storing logs on disk. If a size equal to 0 (zero) is specified, log files are deleted as soon as they are released by a session |
Minimum diskspace free to storage (MB) |
Determines the minimum disk space on a partition to reallocate logs or to start recording on the repository. This is the lower band limit to monitor |
Delete log files older than (days) |
Specifies the number of days during which the files are stored. If this value is equal to 0 (zero), management occurs by size or by minimum number of files |
Minimum number of files (grouped by name) to be kept after deletion |
Specifies the minimum number of files that must be kept on the repository when excluding files derived from the same name. If this value is equal to 0 (zero), management occurs by size or by minimum size of files. A value greater than zero leaves at least this number of files for each group of names, such as "E3*.*" or "E3Server*.*" |
Reset to default |
Restores default values for options, that is, twenty-five percent of a partition's free space, automatic management of space, one hundred eighty days, and two files |
NOTE |
The following routines and the management only occur when there is a need to release files, because their size is reaching the configuration limit in the Limit the diskspace used for storing log files to option. |
The order of execution of repository's file exclusion filters is the following:
1.Creation date: When executing the management, all files with a creation date prior to the maximum allowed in the Delete log files older than (days) option are deleted, starting from the oldest to the newest ones, as long as the size of the files overrides repository's maximum quota.
2.Name pattern: If even after deleting the oldest files of the repository. in the Delete log files older than (days) option, the remaining size is still greater than the limit, files are processed by a name filter, in the Minimum number of files option. In this filter, files are deleted up until the control limit is reached, but preserving at least the configured number of files. This is very useful for establishing a sequence in a regressive analysis of events.
3.Total size of the repository: The last filter executed is by a repository's total size. In this case, if still after performing the previous filters the repository is above its limits, files are deleted from the oldest to the newest ones, until reaching the security limit.