Filename |
DNPSlave.dll |
Manufacturer |
DNP 3.0 Protocol |
Devices |
|
Protocol |
DNP 3.0 |
Version |
4.0.74 |
Last Update |
13/05/2025 |
Platform |
Win32 |
Dependencies |
IOKit v1.15 |
Superblock Reading |
No |
Level |
31201 |
Introduction
This Driver implements DNP 3.0 protocol in Slave mode (Outstation), according to levels 2 (two) and 3 (three).
DNP (Distributed Network Protocol) is an open and non-proprietary communication protocol, based on IEC (International Electrotechnical Commission) specifications, adapted for use in highly secure applications, on moderated speed and amount of data. It is extremely flexible and can be used in any hardware platform.
The model specified by ISO/OSI (International Standards Organization / Open System Interconnection) establishes seven layers for a network protocol. IEC, on the other hand, specifies a simplified model, which is formed only by physical, data link, and application layers. Such model is called EPA (Enhanced Performance Architecture). The next figure displays EPA model's structure and its communication system.
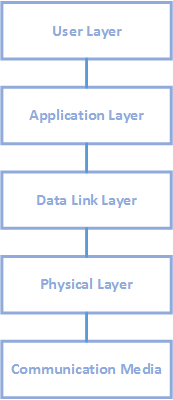
Enhanced Performance Architecture model
A User Layer can be defined as the location where users manipulate data, after all communications. In Elipse Software applications, it is represented by a user application. The user layer uses this Driver's application layer to send or receive full messages to or from a station.
An Application Layer is responsible for specifying in details the requests from the user layer, and back to it when a message comes from the data link layer. In other words, it gathers messages from the user layer, called fragments, into a message of multiple fragments with full information to be processed and sent to a station through the data link layer.
A Data Link Layer is used to pass messages from a primary, or origin, to a secondary, or destination, station. It also packs data, check it for transmission errors, and then send it to the TCP/IP network.
DNP protocol can be configured to exchange messages via polling, or constant communication, or via integrity - change, which is more efficient. Sending changes, also known as RBE (Report by Exception), can occur spontaneously, or not requested, or non-spontaneously by an explicit request from the master side for these changes.